- Configure an Application in Microsoft Entra
- Optional: configure an API in Microsoft Entra
- User experience in the Macrobond application
- Configuring a Web API Series Provider to use OAuth
The Macrobond application version 1.31 and later users can use identities defined in Microsoft Entra to log in to the Macrobond application via OpenID Connect (OIDC). Certain configurations need to be completed by both Macrobond and client for this to function correctly.
- The client must define a new “app” in Microsoft Entra as explained here.
- Macrobond must receive some information about the MS Entra App registration and add this to the client configuration.
- The first time users log in after configuration has been completed, they will need to connect their Macrobond account with their MS Entra account. This process is outlined here.
The Macrobond application must be able to communicate with https://apiauth.macrobondfinancial.com, which is a new technical requirement.
Configure an Application in Microsoft Entra
To be able to connect the Macrobond application to Microsoft Entra, you need to create an “App registration” in MS Entra and provide the Macrobond support team with some pieces of information about the registration:
- Application (client) ID
- Authority URL
- (optionally a “scope”)
Below is a step-by-step guide on how to create an application in MS Entra. There is also some material from Microsoft covering the same topic here: How to register an app in Microsoft Entra ID - Microsoft identity platform | Microsoft Learn
1.Open the Entra admin center
Go to https://entra.microsoft.com/ and log in as a user with access rights to create application registrations.
2.Go to the App registrations section
3.Create new registration
Select “+ New registration”
On the registration form, give the application registration a name, select the supported account type. Do not fill in any Redirect URI yet; it will be done in the next step. Press Register to create the registration.
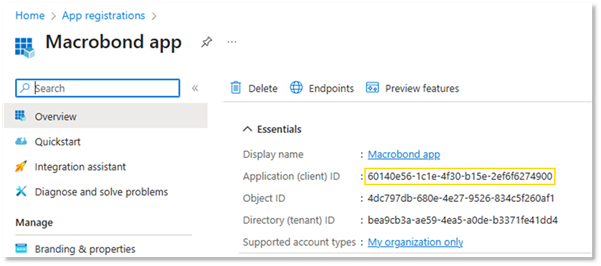
4.Capture the “Application (client) ID”
Go to the “Overview” page for the application registration and make a note of the “Application (client) ID”. This is one piece of the information you should send to Macrobond the Macrobond support team, and it will also be needed in one of the following steps.
5.Add a platform
In the settings for the newly registered application, select the section “Authentication” and then “+Add a platform”.
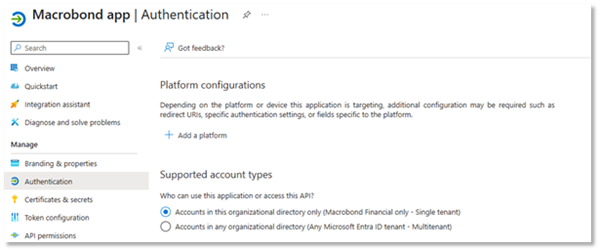
From the list of platforms, select “Mobile and desktop applications”
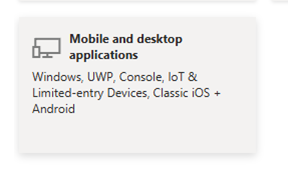
6.Add a redirect URI
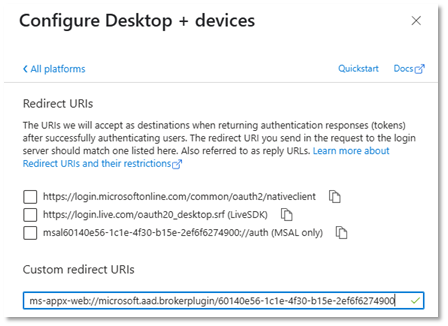
In the platform settings, add a custom redirect URI. The URI should be “ms-appx-web://microsoft.aad.brokerplugin/” followed by the “Application (client) ID” that you can find on the app registration Overview page.
Based on the sample application ID, the redirect URI would be configured as a “Custom redirect URI” like this:
7.Copy the “Authority URL”
Click on Endpoints to show a list of endpoints.
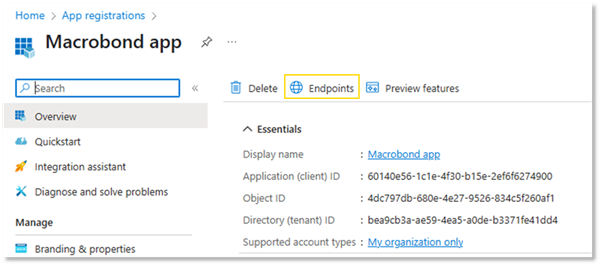
From the list copy Authority URL:
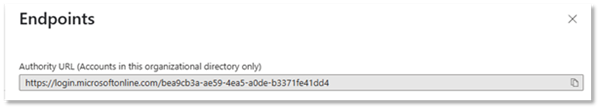
Send the “Application (client) ID” and the “Authority URL” to Macrobond the Macrobond support team who will configure the service.
The application registration is now done, but you might want to do additional configuration.
8.Additional configuration
You probably want to assign the new app to Entra users in the “Enterprise applications” section:
Verify that that the application is granted the permission “User.Read” for Microsoft graph. This is required to be able to sign in to MS Entra. Ideally make sure that “Admin consent required” is set to “No” for the best user experience.

Please note that giving users access to the app in Microsoft Entra will not automatically give them access to the Macrobond application. You still need to have a Macrobond account. Having access to the app in Entra only controls what accounts that can be associated with Macrobond accounts, but you still need the Macrobond account and password to make that association the first time.
Optional: configure an API in Microsoft Entra
If you plan to use OAuth authentication when you connect to your own data sources in the Macrobond application via the Web API Series Provider, you need to also register an API and associate it with the Entra Application defined in the previous section.
Below are the steps you can take to take to register an API, but there is also good description from Microsoft here: How to configure an application to expose a web API - Microsoft identity platform | Microsoft Learn
Use roles…
9.Create the API registration
An API registration starts with registering an application. No Redirect URI should be specified.
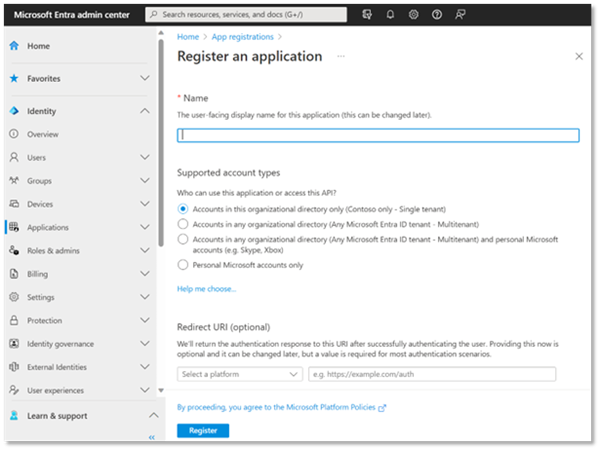
10.Expose and API and connect to the Entra Application
Specify the “Application ID URI”. This typically looks like a URL, but it is used only as a way to create a unique identifier. It will typically include your domain name, since this is already unique to you, plus something that identifies your Web API Provider servers. You might already have a pattern for creating such application/API IDs.
Next you need to add a “scope”. You can use scopes for access controls, but it might be easier to have just one scope that represents the service and then use the group membership for this purpose.
Finally, add the client application. Use the “Application (client) ID” from the app registration you made earlier in this guide.
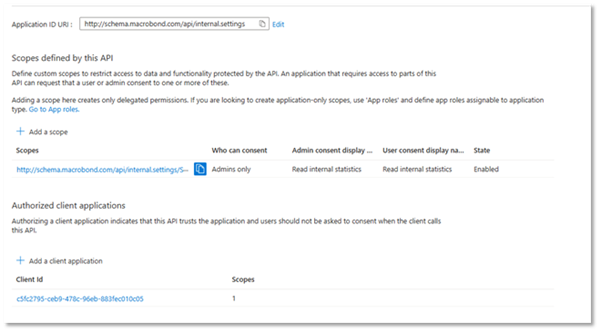
Copy the full scope identifier and send this to Macrobond the Macrobond support team whothat will add it to the configuration.
In the screenshot example above this would be “http://schema.macrobond.com/api/internal.settings/Statistics.Read” but for you, it should be something based on your domain and scope.
11.Optional token configuration
Depending on how you want to do authorization in your Web API Series Provider service, you might want to include additional information in the security token passed on to the API server. Such configurations are done in the “Token configuration” section of the API registration.
For instance, it is common that you want to include the “aud” claim in the JWT. This will add the “Application (client) ID” value to the “aud” claim in the tokens.
Another claim you might want to add is “groups”.
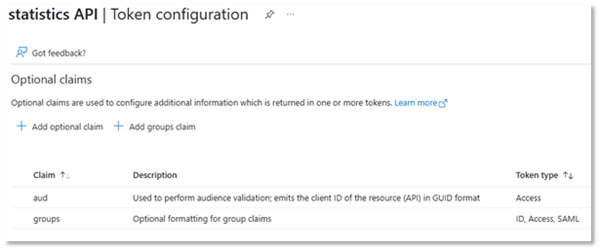
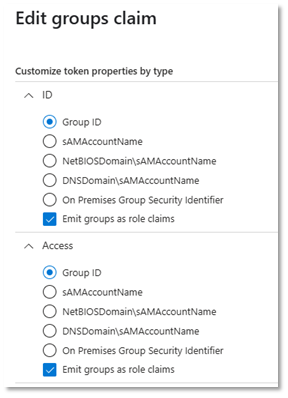
The “groups” claim will include a list of security groups that the user is a member of in the token. (There are some caveats here if the list is too long. The Microsoft documentation should explain the options here.)
User experience in the Macrobond application
The user will have a Macrobond account username and a MS Entra username. These are often the same name in the form of an e-mail address, but they might be different.
When you enter your Macrobond username in the Macrobond application, the application will detect that this user is configured to use MS Entra and will show a “Login” button.
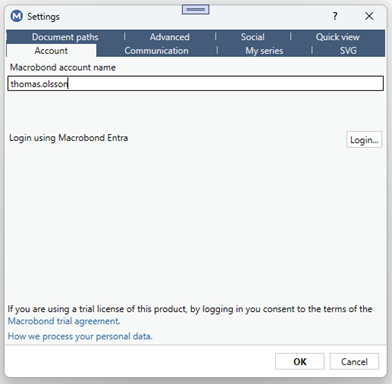
You will be asked to log in to MS Entra in your web browser.
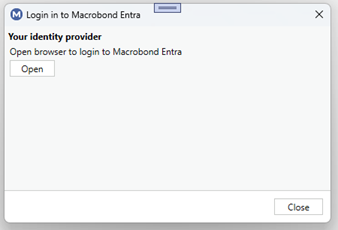
Once logged in to MS Entra and your accounts are already connected, you are good to go.
If your accounts are not connected, you will be prompted for your Macrobond account password. It might be filled in already if you have logged in on this computer before your account was configured to use MS Entra.
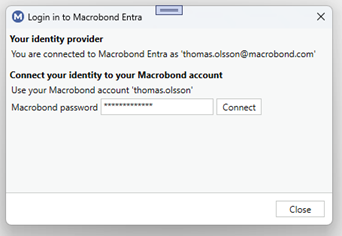
If your password matches when you press “Connect”, you will get a confirmation.
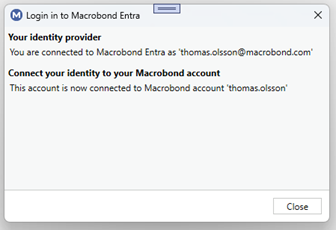
Press “Close” and then “OK” to start using the application.
The Macrobond account and the MS Entra account are now connected. In the rare event that you want to disassociate a Macrobond account from an account in MS Entra, please contact the Macrobond support team.
Depending on the configuration of MS Entra, the session might expire, and a new interactive login is required.
In this case, you might see a message like this in the application:
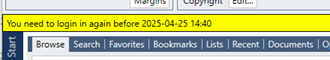
This means that the application has detected that the token cannot be renewed without user interaction, but we still have a cached valid token a while longer. Pressing the yellow bar will open the Settings dialog and it will look like this:
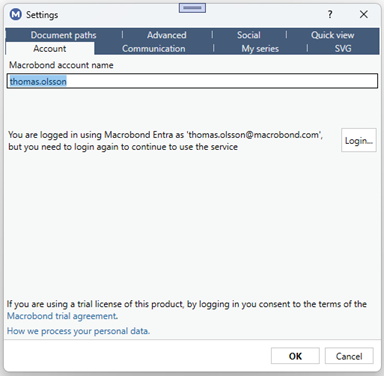
The COM API (MATHLAB, Python etc.) and EViews add-in do not support interactive login, so you might want to keep the Macrobond application running if you are using those services. This is also true when you update charts in Microsoft Office documents.
Configuring a Web API Series Provider to use OAuth
There is a new setting in the configuration file for WebAPI Series Providers called “UseOAuth” that will make the application include the access token from MS Entra in the request as the http header “Authorization: Bearer”.
<?xml version="1.0" encoding="utf-8"?>
<web:WebApiSeriesProvider xmlns:web="http://schemas.mbnd.eu/2019/webapiseriesprovider">
<web:Host>http://myseriesapiserver.com</web:Host>
<web:UseOAuth>true</web:UseOAuth>
</web:WebApiSeriesProvider>